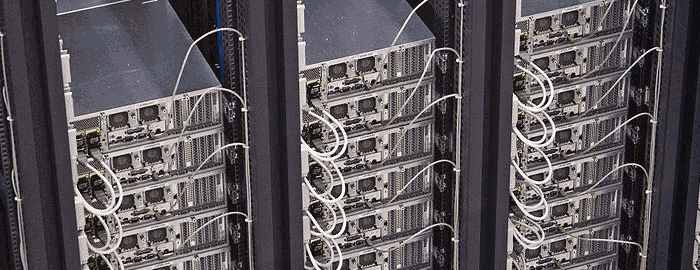

Penetration testing is an all-encompassing test of your organization's security posture. Wombat Labs will inspect your organization from end to end attempting to find unauthorized or unexpected ways in. By testing the strength of your digital assets in a controlled environment, you can find and fix weaknesses before they are discovered and exploited by malicious attackers.
Wombat Labs offers a complete array of testing services including wireless emissions analysis, network enumeration, and personnel authorization assessments. We can either work with your existing IT department in a fully visible "white-box" test, or perform a more realistic "black-box" test, where no information is given beforehand, and your IT department is not alerted in advance to the tester's presence.


Wombat Labs will find and correct the unexpected bugs that are present in every body of source code. Software products are produced in an environment where time-to-market is key, and meeting the business requirements of the stake holders is the chief priority. Unfortunately this typically means security concerns can be either overlooked or bolted on as an afterthought.
There is a sense of how a particular program "should" work; however if aspects of the program were designed incautiously, it can lead to back-doors where an attacker could monitor or steal the critical business assets that your software is working with. Wombat Labs offers both static and dynamic code analysis as well as recommendations for mediating vulnerabilities.

You have specific business requirements that you need to meet. There is often a variance between these requirements, and the architectural capabilities of systems that are put in place to meet them. Wombat Labs will help assess and document these variances and make recommendations as to the feasibility of a system meeting the specified requirements.
Knowing what your systems can and cannot do is fundamental. An unmet capability may be acceptable for routine operations but may mean the difference between success and failure in extraordinary circumstances. When your systems cannot do what you ask of them, that indicates a failing of the "availability" component within the triad of security.

All software eventually becomes outdated as vendors produce new versions. Vendors routinely release "patches" that fix security vulnerabilities or improve the usability of their applications. Your business has dozens of pieces of software, all of which need to be updated when their patches come out.
Wombat Labs will keep track of what software your business is using and help you manage the update processes. When your business depends on all sorts of interlocking components, it becomes more difficult. Updating one piece of software to the latest version might break the connections it makes with another aspect of your business. We will help you perform dry-runs of updates in controlled environments and verify that interoperability remains uninterrupted.


Do you trust all of your employees with your business plans? Can anyone who works for you see the credit card information you collect? Do you keep confidential information that you're legally obligated to protect? Wombat Labs will identify what information is needed by which employees to get their jobs done. We help you ensure that people may only see what they are permitted to see.
It's important to trust the people you work with. Unfortunately, it's also important to consider the possibility of insider threats. By clearly delineating access, you greatly reduce the number of possible causes in the event a data breach occurs. For particularly sensitive matters, breaking a task into several distinct parts makes it less likely that any one employee will be able subvert the process.


You have a computer with all of your important records on it and today it won't boot. You've heard about the importance of backups but never got around to them and now hundreds of hours of productivity are lost.
Like security itself, backups are an ongoing process rather than a single step performed once. If you last backed everything up in 2007, that won't have your currently relevant work. If you have a backup process, but new work isn't added to it, then that work isn't going to be there when you need it. If you back everything up but don't practice restoring, then you don't know if the process will work end to end.
Wombat Labs will help you navigate this process efficiently and will give you the peace of mind that a non-operational computer is nothing more than a slight annoyance.


Passwords are perhaps the single most vexing aspect of security. They need to be long and complex. They can't be your dog's name. They can't be written down and kept under the keyboard.
These seemingly arbitrary rules are what determines the "strength" of a password. Wombat Labs will show you the best practices that let you have strong passwords without the headaches that come with them. We will audit all of the assets you have which are currently protected by passwords. We'll determine who has access, when the passwords were last changed, and if there's a possibility of unauthorized access. If appropriate, we will demonstrate alternative methods of authentication which maintain a high degree of access control without the downsides of typed passwords.

It's easy to find news stories about laptops left in taxis or other public places. These stories are newsworthy because sensitive data was on the laptop and is now in the hands of persons unknown. Encryption can't solve the problem of careless employees, but it can render the data useless without the key. Whole Disk Encryption means that the computer won't even turn on without the key.
Encryption is tricky to do right. Some algorithms are not as mathematically secure as others. Some are secure, but only when the right configuration options are used. Some were considered secure but have been found to be breakable by newly developed techniques.
Wombat Labs will help you be sure that you're encrypting the right things using the right methods.

Mobile devices are everywhere. Tablets are becoming increasingly ubiquitous, and smart-phones are replacing the simpler phones in people's pockets. All of these devices can be considered full fledged computers. They are extremely portable, have large amounts of storage, connect to networks indiscriminately, and are considered a standard part of life in 2022.
Wombat Labs will help you determine the challenges that mobile devices present to your business and how to address them. Being small, they're the perfect vehicle for slipping confidential data out the front door. Since they connect equally well to your network and the rogue network at the coffee shop, they can bring malware into your organization that would otherwise be stopped by your network defenses.

Risk management is the categorization and mitigation of threats which affect your business. Every endeavor faces risks that can prevent it from succeeding, and an appropriate response to one threat may not be appropriate to another.
Wombat Labs will talk to you about the goals you're implementing and what the corresponding pitfalls are. We then will discuss with you various responses to these pitfalls so that you can move forward with greater certainty.
Some threats require an immediate response.Others require a more long term solution.Still others can be deferred indefinitely as long as other conditions don't arise.We'll help you know the differences between them.