The Security Action Plan is the core document which will shine light into the unknown areas of your network and systems. Wombat Labs will provide your company with a detailed list of all problem areas detected along with proposed solutions to correct the deficits.
Threats are categorized by two aspects: likelihood of occurrence and potential damage. If something can do catastrophic damage but is unlikely to happen, then it needs to be fixed but there's no need to panic. Something that does minimal damage but happens on a daily basis isn't cause for panic either but it also needs to be fixed.
A threat that is both likely and can cause catastrophic damage needs to be fixed today. Wombat Labs will help you do it.
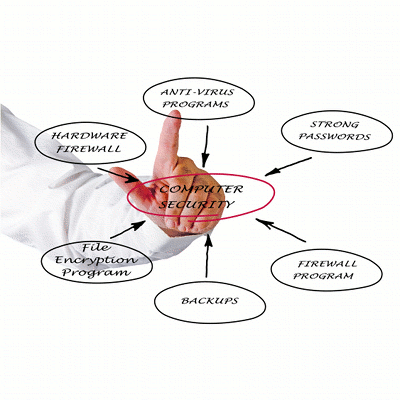
One of the most important aspects of having a security assessment is the construction and incorporation of a security policy custom built for your company. With the information Wombat Labs receives during the assessment, and with the involvement of your key staff, we will help you build a policy that meets your needs and is compliant with security best practices.
Balance is important.
If your policy doesn't consider the needs of your users and customers, then it will be resented and worked around. If your policy isn't well defined, then it won't adequately protect you from threats. This is a difficult balance to create, and we'll help you find it.


Employees are an integral part of your business success. It's often quoted that "people are the weakest link in matters of security". Less quoted is the fact that informed people are the strongest link in the security chain.
Poorly trained users will click on things they shouldn't. Their computers will be hijacked by malware without them even being aware of a problem. The machine will just be "running slow". Well trained users will know what looks right and what looks suspicious. They will know to speak up early if something seems wrong so any damage is minimized.
Wombat Labs will provide you and your employees with fun and interactive security and training on topics relevant to your business. Your employees will remain your greatest assets.


Planning ahead for security incidents is an often overlooked best practice. Wombat Labs will help you to document and internalize the various procedures to follow when (not if) such an event occurs. These procedures include your incident response plan, backup response plan, business continuity plan, and breach notification data requirements.
Just as a family has plans for what to bring and where to meet in case of a fire, so your business should have a documented and orderly response to cyber-security disasters.
The moments after damage has occurred are the most critical. They are also the worst possible time to panic. Knowing what to do, and calmly implementing the specified procedures will minimize loss of your customers, revenue and reputation.


Being secure is a continuous process. Your security posture changes every time new computers are added to your network. It changes every time you hire and fire employees. It changes every time you choose a service provider and outsource some of your work. Growth itself is change, and as you grow, your security posture will need to grow as well.
After our assessment you will have much greater control over the factors that lead to a position of security. Your business will inevitably change, but you will be able to direct those changes with confidence and certainty.
That confidence and certainty will be present in the form of your security policies, your employee training materials, and your contingency plans.